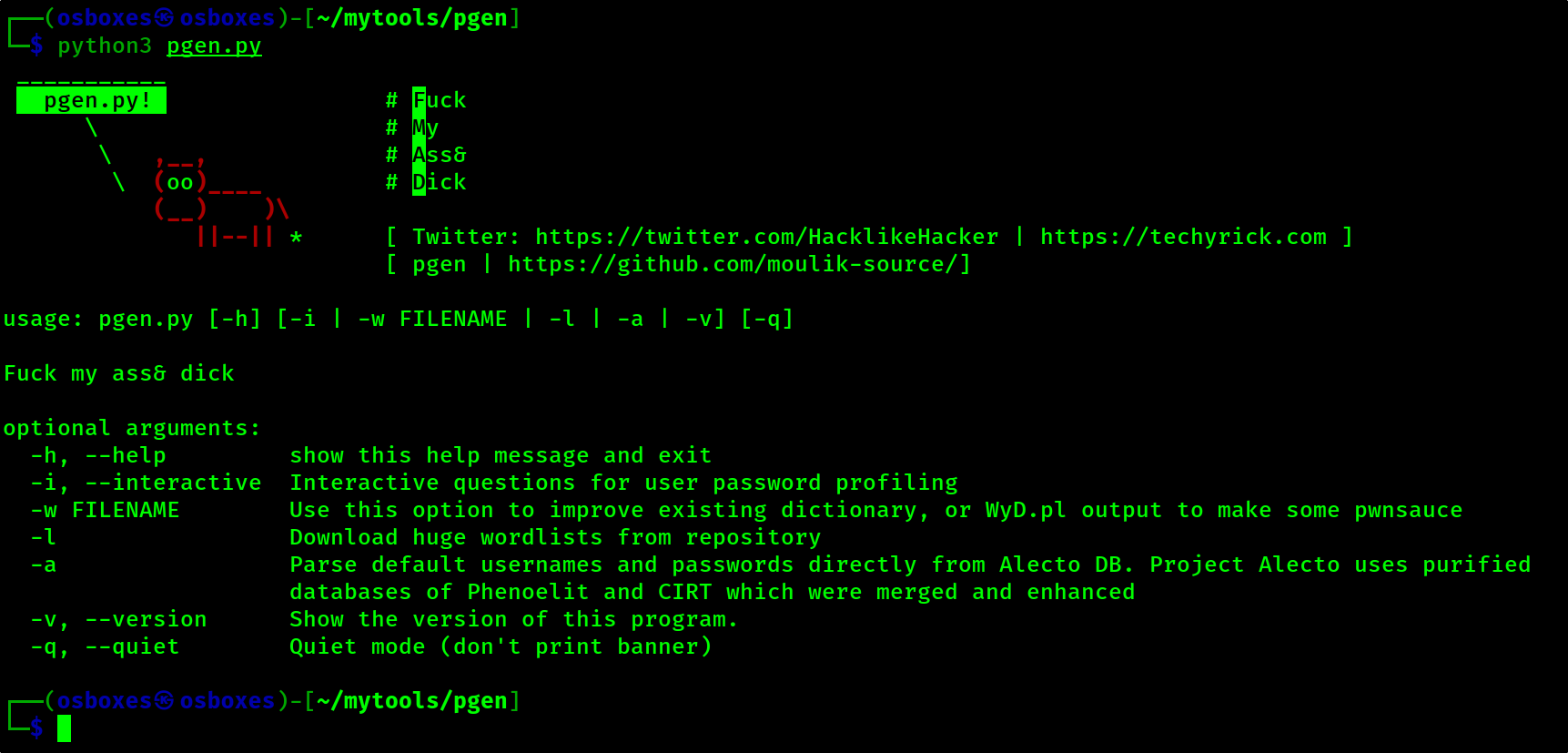
pgen
Pgen is the best brute force password generator and it is improved from the cupp.py
The pgen tool is dedicated to Leonardo da Vinci
-Time stays long enough for anyone who will use it.
Installing
git clone https://github.com/moulik-source/pgen/
ls
cd pgen
python3 pgen -i
Interface
Disclaimer
The use of this tool is your responsability. Use parsero to audit your own servers or servers you are allowed to scan. I hereby disclaim any responsibility for actions taken with this tool.
Author
- Moulik
- Blog: http://techyrick.com/blog
- home page: http://techyrick.com
- contact: http://techyrick.com/contact
Donate
0x4aa154fa7bFBA692233b987b500Ae51BC1D11B88